
Jhoose Security - Update to include recommended security headers.
I have updated the module to automatically add the OWASP recommended security headers to the HTTP response.
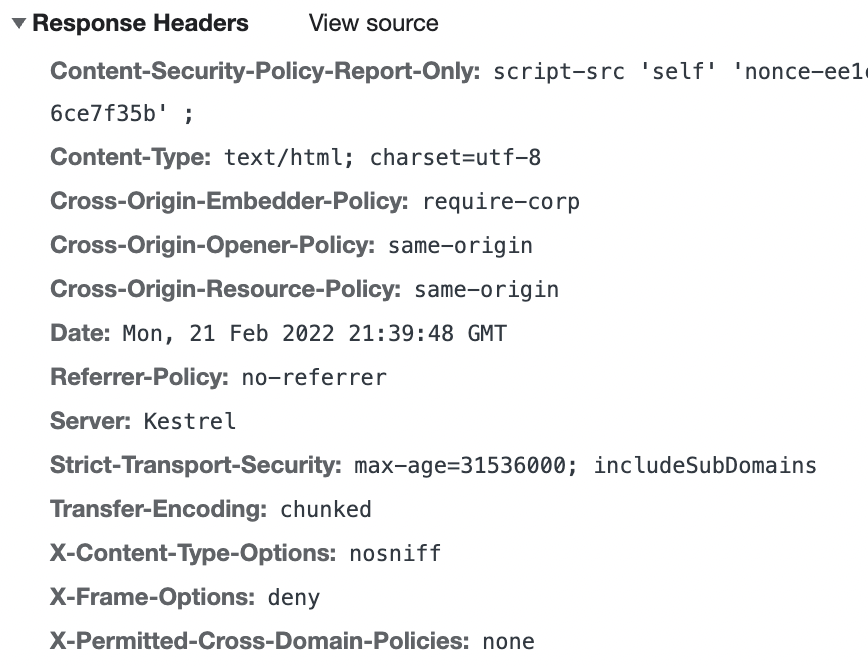
These headers are automatically added to the response but can be configured as required, or even disabled.
Code Configuration
1 services.AddJhooseSecurity(_configuration, (securityOptions) => {
2
3 // define the XFrame Options mode
4 securityOptions.XFrameOptions.Mode = XFrameOptionsEnum.SameOrigin;
5
6 // disable HSTS
7 securityOptions.StrictTransportSecurity.Enabled = false;
8 });Configuration via appSettings
1"JhooseSecurity": {
2 "ExclusionPaths": [
3 "/episerver"
4 ],
5 "HttpsRedirection": true,
6 "StrictTransportSecurity": {
7 "MaxAge": 31536000,
8 "IncludeSubDomains": true
9 },
10 "XFrameOptions": {
11 "Enabled": false,
12 "Mode": 0,
13 "Domain": ""
14 },
15 "XPermittedCrossDomainPolicies": {
16 "Mode": 0
17 },
18 "ReferrerPolicy": {
19 "Mode": 0
20 },
21 "CrossOriginEmbedderPolicy": {
22 "Mode": 1
23 },
24 "CrossOriginOpenerPolicy": {
25 "Mode": 2
26 },
27 "CrossOriginResourcePolicy": {
28 "Mode": 1
29 }
30 }Managing the server header
The security module doesn't remove the 'server header', this may seem strange, but the approach differs depending on how you are hosting your site. I have included some examples below.
Another consideration, if you are hosting your solution with Optimizely DXP then the CDN will automatically remove the header.
Kestrel
1return Host.CreateDefaultBuilder(args)
2 .ConfigureCmsDefaults()
3 .ConfigureWebHostDefaults(webBuilder =>
4{
5 webBuilder.ConfigureKestrel(o => o.AddServerHeader = false);
6 webBuilder.UseStartup<Startup>();
7});IIS
1<?xml version="1.0" encoding="UTF-8"?>
2<configuration>
3 <system.webServer>
4 <security>
5 <requestFiltering removeServerHeader="true" />
6 </security>
7 </system.webServer>
8</configuration>Installation
dotnet add package Jhoose.Security.Admin --version 1.1.1.89