
Introducing Jhoose Security - A module to manage your Content Security Policy
It has always been challenging to manage the Content Security Policy (CSP) on a website; this new module for Optimizely aims to simplify the process, giving advanced editors more control.
Features
Interface to manage policies.
Global 'report only' mode, or specify for each policy.
Add 'nonce' to inline script or style tags.
Ability to specify paths that are excluded from outputting the policy header.
Administration
Once the module is installed, you will see a new 'Security' menu item within the top menu.
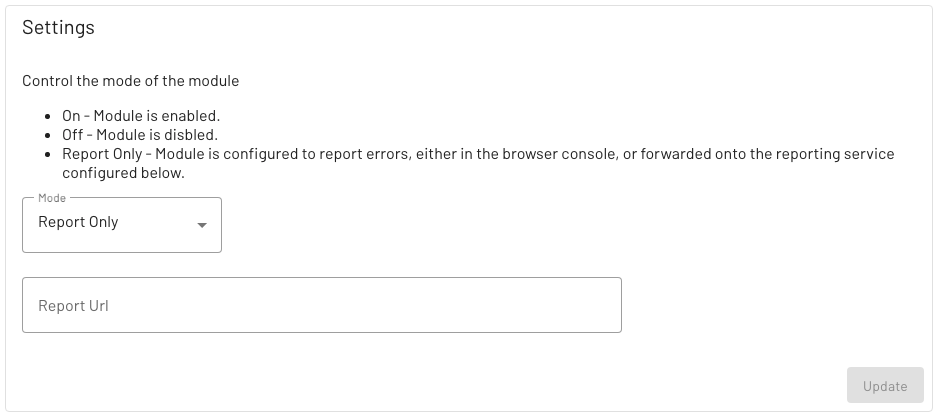
Settings
This screen gives you access to the global settings of the module, allowing the module to be enabled/disabled or switched into 'Report Only' mode.
It is also possible to specify an endpoint for a reporting service.
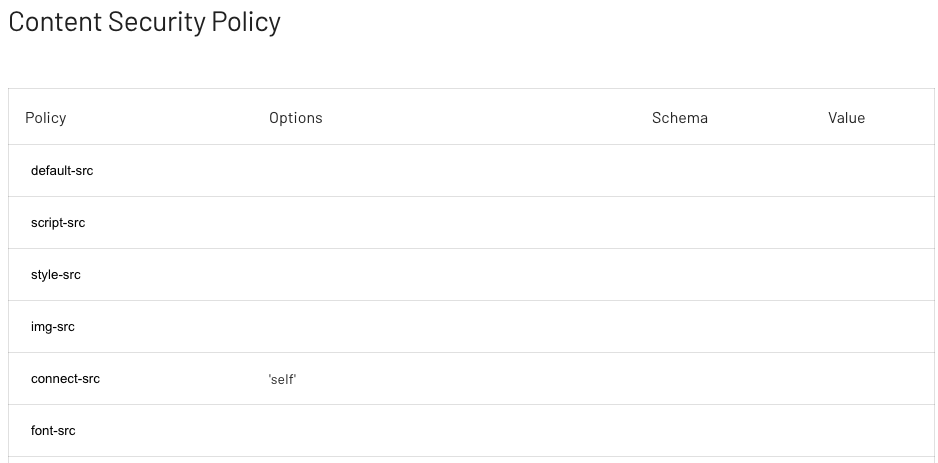
View Policies
All security policies are listed, with a summary of the policy configuration. A user is then able to click on a policy to view the policy in greater detail or amend it as required.
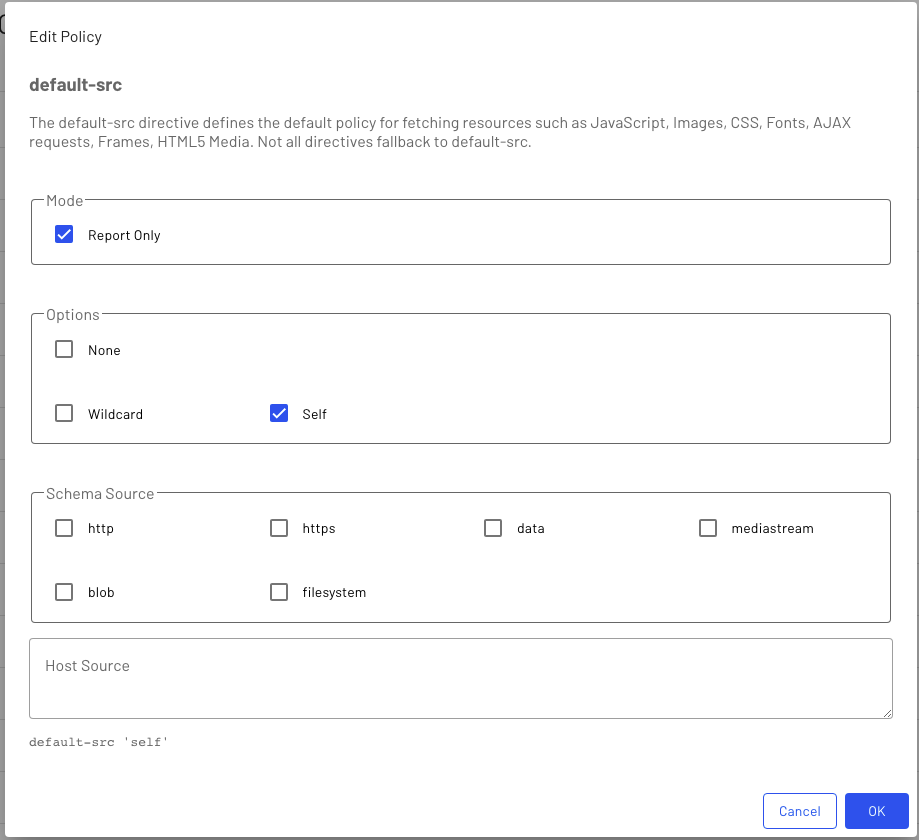
Edit Policy
This screen allows users to manage individual policies; these changes will be saved when the 'OK' button is pressed.
When changes are made, it is recommended that they are tested in 'Report Only' mode, which ensures that nothing is adversely impacted by the new configuration.
Installation
Install the package directly from the Optimizely Nuget repository. This will install the admin interface along with the middleware to add the CSP header to the response.
Github: https://github.com/andrewmarkham/contentsecuritypolicy
dotnet add package Jhoose.Security.Admin
Configuration
Startup.cs
1services.AddJhooseSecurity(IConfiguration configuration, Action<SecurityOptions> options = null);The `Action<SecurityOptions> options` is optional, and if not specified, then the default will be used.
1 "JhooseSecurity": {
2 "ExclusionPaths": [
3 "/episerver"
4 ]
5 }ExclusionPaths: Any request which starts with a path specified in this property will not include the CSP header.
app.UseJhooseSecurity();
Nonce Tag Helper
It is possible to get a nonce added to your inline <script> and <style> tags.
_ViewImports.cshtml
1@addTagHelper *, Jhoose.Security.Core
2<script nonce src="/assets/js/jquery.min.js"></script>
3